Information Technology
Information Risk Analysis and Information Systems (IT Security Risk Assessments)
The «IT Risk Assessment» is a workshop aimed at identifying risks to the security of information systems that have direct and indirect impact on the functioning of the company but also its reputation. The «IT Risk Assessment» is structured around the areas of security standard ISO 27001. Typically the areas included are:
- Management of IT security
- Physical and environmental security
- Design and Information Security Policy Development and Information Systems (Policies and Procedures)
- Management of security incidents
- Safety of human resources
- Management of IT assets
- Business continuity
- Access Control
- Compliance
- Acquisition, development and maintenance of information systems
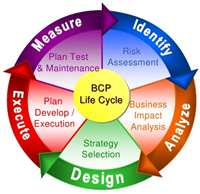
Business Continuity Plan (BCP / DRP)
The «Business Continuity Plan» describes the processes and procedures designed and implemented by a company in order to ensure that key functions will continue to be in force, both during and after a disaster.
Penetration testing and examination of vulnerabilities (Penetration Testing and Vulnerability Assessment)
The «Penetration Testing» is the procedure followed so as to identify vulnerabilities in the information systems of the company, in order to steal important information or application malicious actions.
Payment Card Industry Data Security Standard (PCI DSS)
The «PCI DSS» developed as an industry standard for enhancing the security of personal data on payment cards, consumer protection and reduce fraud probability using the card. The model is structured around six (6) different security objectives, as follows:
- Implement and maintain a secure network
- To protect data holders
- Implement a vulnerability management program
- To enforce strict access control measures
- To maintain a strict information security policy
All organizations that maintain, process or dispatch elements of payment cards must comply with the standard «PCI DSS». With the help of our specialist staff providing risk management IT services, you can now manage a critical area of the daily operation of your business safely and effectively.